Sommaire
Kidnapping of Ledger co-founder: what about the personal data of wealthy executives?
On 21 January 2025, David Balland, co-founder of Ledger, and his wife are kidnapped from their home by an armed commando. Ransom demanded: $10 million in cryptocurrency. A scene from a film. But behind this drama, we can't help but wonder: how did the criminals know where to go?

David Balland was not a flamboyant crypto entrepreneur, flaunting his success on the networks. Not the type to feed an Instagram account between Lamborghinis and seminars in Dubai. He led a quiet life, far from the spotlight. Yet his kidnappers seemed to know exactly where to strike.
Addresses recovered from leaked databases, files accessible on official registers, metadata left on sites without a second thought. Personal data has become a physical risk factor.
What types of data?
Manon El Assaidi, our Director of Operations, has dealt with many cases of this type using what is known as 'OSINT' (Open Source Intelligence).
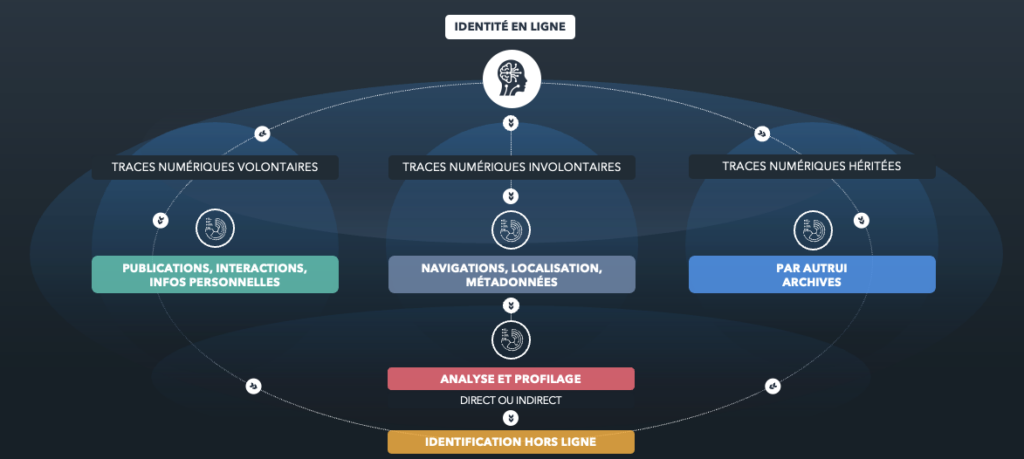
There are three types of digital traces:
- Voluntary digital traces: information that we intentionally share online, such as posts on social networks.
- Unintentional digital traces: data collected without our explicit intention, such as metadata associated with files or browsing information.
- Inherited digital traces: information about us published by others, such as photos or mentions.
These traces can reveal sensitive information. For example, a photo of a house shared on a social network (voluntary trace) may contain geolocation metadata (involuntary trace), potentially exploitable by malicious individuals.
It is therefore essential to manage these traces carefully to protect our privacy and security online.
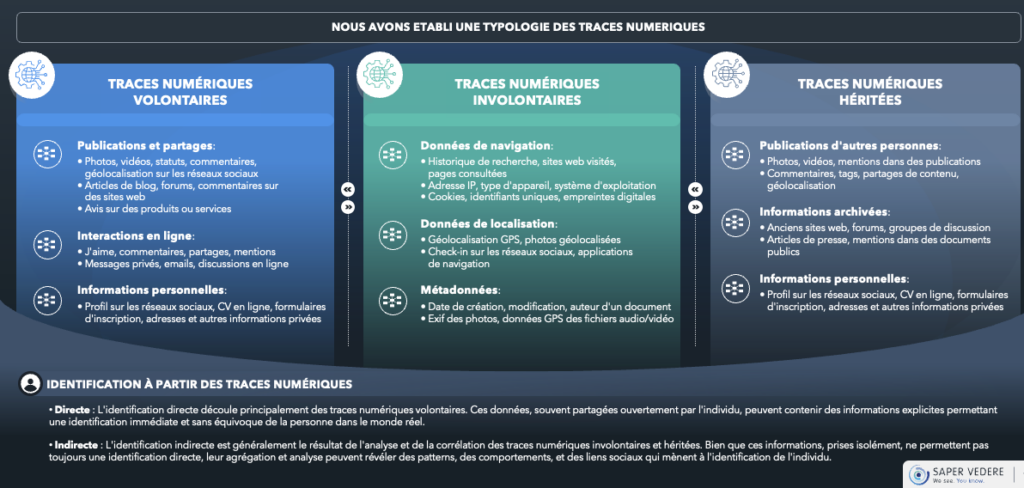
How can we use data to move from one metadata to another?
We search for specific data via various elements, then exploit common variables between two metadata networks to obtain additional information about someone.
For example, I identify the name of an executive in company data. This executive has a presence on LinkedIn, where I retrieve his previous positions and the people with whom he interacts. From this, I identify brothers and sisters. These siblings have photographs on Facebook showing a family dinner, with data enabling me to geolocate the executive's home.
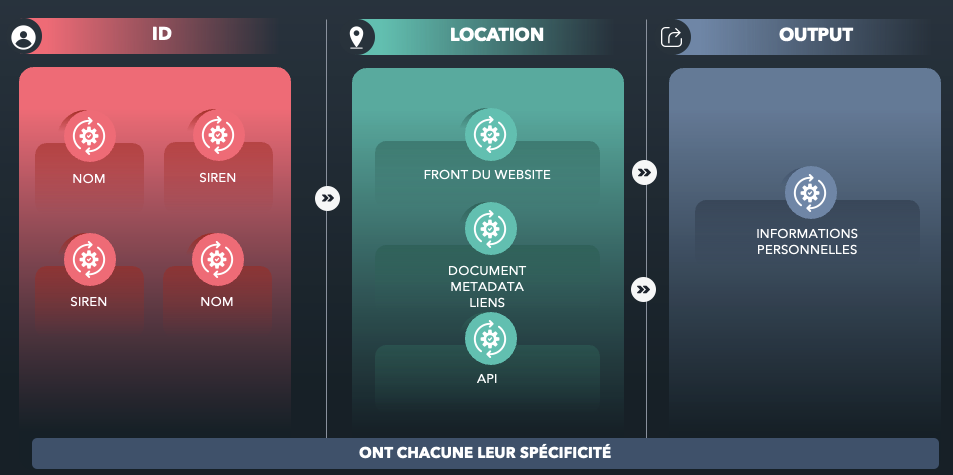
Examples of this can be found in company databases:
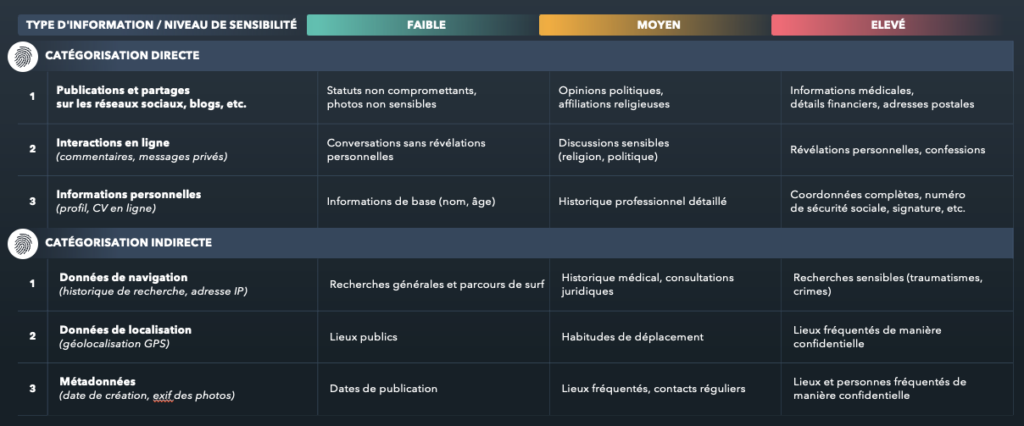
Obviously, some data are of little interest or sensitivity and some are highly sensitive:
Artificial intelligence will make this even more accessible
Artificial intelligence can process this previously inaccessible data massively, automatically and exhaustively. By sending hundreds of pre-set prompts to dedicated sources. On the other hand, at a very basic level, we can already obtain some information:
And let's adopt it in this case:
If I want to work with visuals, videos or anything else, I already have a list of things to look at:
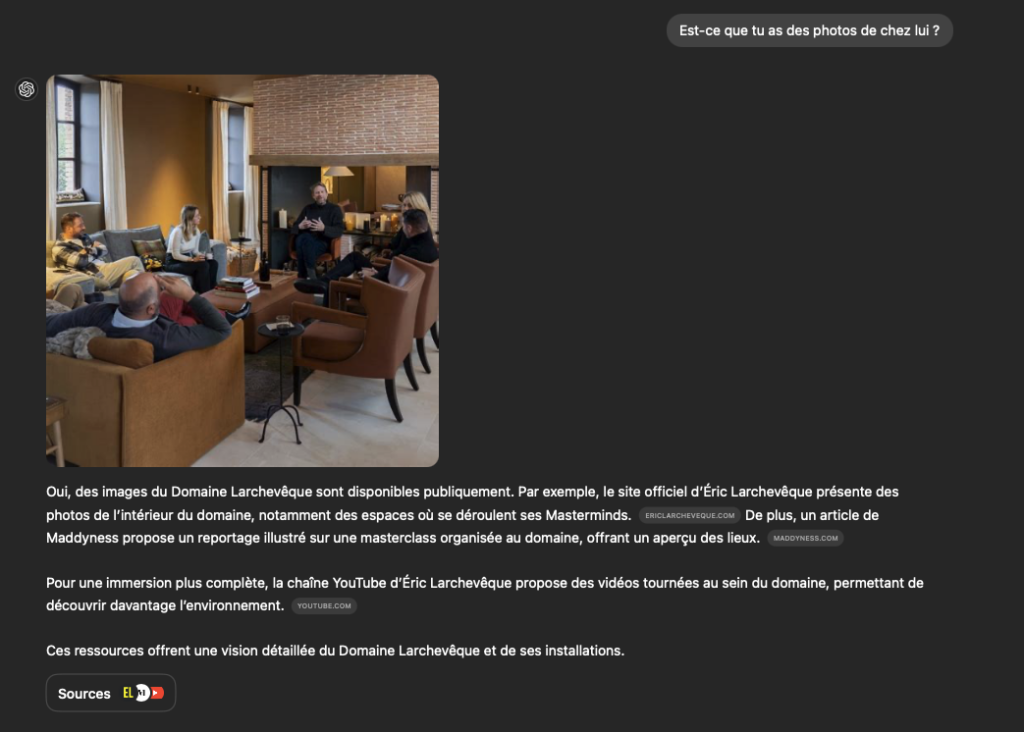
In a town with a population of 1001 (in 2021), there's a good chance you'll bump into him outside the seminars he gives in his field!
What are the issues?
Once the theoretical elements have been explained, it has to be said that there are a whole series of problems:
- Framing differentiation: How can you see the harm in publishing a family photo? How can we see an administrative paper on page 25 of Google as a concern for our digital reputation? Many companies and individuals mistakenly think that information is protected simply because it is buried in the mass of public data. But OSINT tools make it possible to automate searches and make the invisible visible.
- Dissymmetry between offence and defence: Protecting one's data requires constant vigilance and substantial resources, whereas someone looking for information only needs a single vulnerability to exploit a target. Moreover, there are many points of entry: in the case of Ledger, the kidnappers did not attack Eric Larchevêque. And there were other possibilities.
- Difficulty of action: while a survey will always reveal sensitive data, it is impossible to predict that a study will produce interesting results. And even if highly sensitive data is uncovered, the ability to act on it is rather limited.
- Lack of regulation on the subject: the transparency of company registers is important, the right to information also exists, but there is no framework to arbitrate these elements. And embarking on legal proceedings will directly generate a Streisand effect(by trying to prevent the disclosure of information that some would like to hide, the opposite result occurs, i.e. the hidden fact becomes common knowledge).



